Cybersecurity
in the
Infrastructure Industry
You’re our transportation and public water lifeline – and we are here to protect you!
62%
increase in cyber incidents in the (waste-) water industry, making it the highest ranked industry in the US.
(Source: Department of Homeland Security, "ICS-CERT Monthly Monitor," October 2019)
117M
new Malware variants discovered in 2022.
(Source: BSI, 2022)
177Controls
have been published by the National Institute of Standards and Technology (NIST) for IT/OT Security.
(Source: NIST, 2023)
Challenges of the Infrastructure Security
With a small team and limited resources, it can be difficult to keep up with ever-changing threats. Our security solutions ensure that your critical infrastructure is protected and water supply is maintained. You can rest easy knowing you are saving time and money. Whether you are dealing with budget constraints or understaffing, we have the expertise to protect your assets from cyber threats.


“Securing critical infrastructure is about safeguarding more than assets; it's about ensuring the safety and reliability of essential services that communities rely on every day.”
Ozan Dayanc
Product Manager CybersecurityIdentify and Respond to Threats
in Infrastructure Networks
in Infrastructure Networks
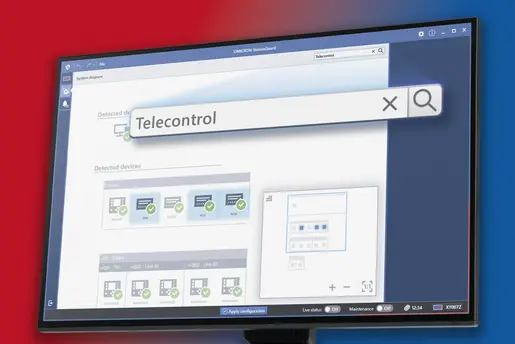
We help you keep your railway and water treatment systems protected from cyber threats. Our range of security services includes thorough security assessments, meticulous functional monitoring, intrusion detection systems (IDS), vulnerability management, audit preparation, and unwavering defense support. Our solution provides visibility, deep packet inspection (DPI), and expert guidance to help analysts investigate potential incidents, setting us apart from the competition.
Security Risk
Assessment
- Receive a comprehensive report on critical assets and potential security threats
- Gain actionable recommendations to mitigate risks
- Improve overall grid performance and functional resiliency
- Sustain ongoing support to ensure continued security
Planned Out from Start to Finish
Together we ensure that your organizational, procedural, and personal factors are taken into account. Standardized escalation plans and role descriptions will help you react quickly to security events.
Functional Security Monitoring Made Easy
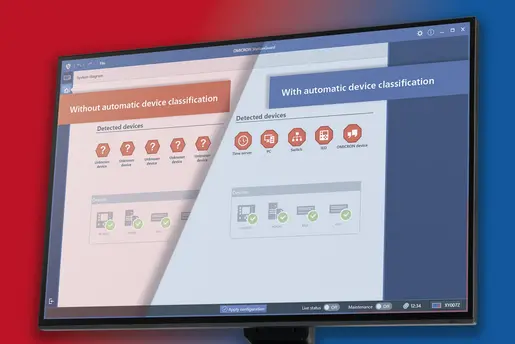
Our functional monitoring ensures that your systems operate as intended, while our IDS guarantees accurate and complete asset inventory and full information security of the operation. Minimizing false-positive notifications is one of our solution’s key features.
Prioritize Risks with Confidence
Our vulnerability management system minimizes risks and vulnerabilities in your system, providing support for audit preparation and defense with our audit checklist for the IDS and training opportunities. If needed, we also offer SOC/SIEM integration.
Resources
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?