Network and energy system operators are legally obligated to ensure cyber security. The German IT Security Act and the German Energy Industry Act stipulate that they must comply with the "state of the art" to effectively manage cyber risks. The NIS2 Directive and the Swiss ICT minimum standard also require this. But what exactly does this mean in practice, and how is "state of the art" defined in vulnerability management?
What "State of the Art" Really Means
The aforementioned laws initially require energy providers to certify an information security management system (ISMS) and implement up-to-date systems for detecting attacks. The goal is clearly defined: to be able to identify and defend against potential threats on an ongoing basis. However, the exact implementation often remains an area of intense discussion.
The answer to the question of what is meant by "state of the art" can be found in various standards and guidelines. The BSI IT-Grundschutz Compendium, for example, mandates that established vulnerability management is a basic requirement. This implies that regular reports from manufacturers, as well as information from authorities and the media, must be incorporated into the security strategy.
Organizations such as the German TeleTrusT take this a step further, emphasizing the importance of constantly monitoring a wide range of sources, from CERTs to newsgroups, in order to proactively identify and remediate vulnerabilities. Standards such as ISO 27001, ISO 27002, and ISO 27019, which is particularly pertinent to the energy sector, provide detailed guidance on how organizations should manage technical vulnerabilities, assess their risks, and implement appropriate countermeasures.
It is also important to recognize the necessity for close collaboration between operators and manufacturers of critical protection and control devices. The EU Cyber Resilience Act underscores this by requiring manufacturers to report vulnerabilities within 24 hours and demonstrate a long-term commitment to the security of their products.

What Are the Implications for Those Responsible in OT and IT Security?
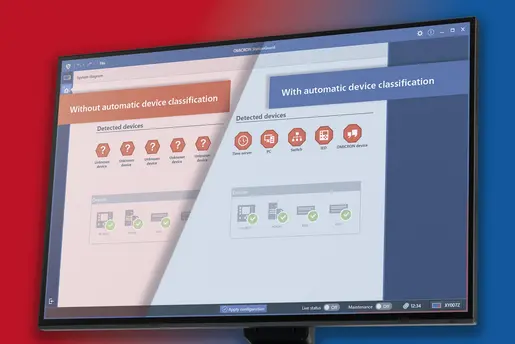
It is of the utmost importance to comprehend the legal and normative framework within which one operates and to actively implement the minimum required security standards. Nevertheless, contemporary vulnerability management, which is not limited to compliance with minimum requirements but is geared towards the company's own risk exposure, is of critical significance. This necessitates continuous monitoring, taking into account all relevant sources of information based on an up-to-date (and complete) asset inventory.
Finally, companies should invest in technologies and processes that enable the reliable detection of vulnerabilities and a rapid response to them. It is important to make sensible use of both internal resources and external expertise to continuously improve one's own cyber resilience.
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?