Why Windows Devices Pose Risks in OT Networks
Targeted by Malware
Windows devices are often the primary targets for malware and ransomware attacks due to their widespread use and known vulnerabilities. The infamous WannaCry ransomware, which exploited a vulnerability in the Server Message Block (SMB) protocol, is a prime example. Such attacks can disrupt critical industrial processes, leading to significant operational and financial impacts.
Inadequate Security Configurations
Unlike dedicated OT systems, Windows devices may not always be configured with stringent security measures. This can result in unauthorized access, system compromise, and potential process disruptions. The default settings on Windows devices often activate various services and protocols that, while useful in general IT environments, can introduce vulnerabilities in OT settings.
Third-Party Tools
It is common practice for Windows devices to utilize third-party tools in order to enhance functionality, convenience and meet specific requirements. While these tools can improve security and operational capabilities, they may also introduce vulnerabilities or conflicts if not integrated or tested carefully within the OT network.
Default-Activated Services and Protocols as Attack Vectors
One notable security risk associated with Windows in OT networks is the presence of services and protocols enabled by default. While these can streamline setup in dynamic networks, in OT networks, where configurations are largely static, they can introduce new (or known) attack surfaces. The following examples outline some protocols and services that warrant particular attention:
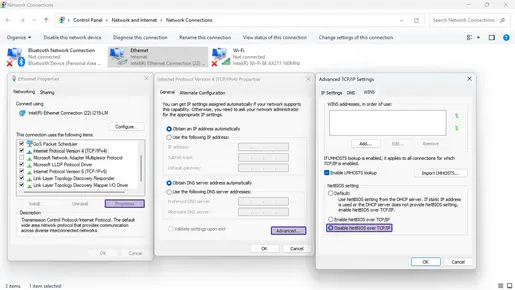
File and Printer Sharing for Microsoft Networks (NetBIOS)
Attack Vector: Vulnerabilities in file sharing protocols can be exploited to gain unauthorized access to sensitive files, distribute malware, or move laterally within the network.
OT Usage: It is typically unnecessary for OT systems to engage in frequent file sharing, which is more common in office environments.
Remote Desktop Services (RDP)
Attack Vector: RDP is a common target for initial network access. This has been observed in the context of ransomware, for example.
OT Usage: In OT environments, remote access is typically used within the network for configuration purposes. However, it should not be used from outside the local network.
Windows Remote Management (WinRM)
Attack Vector: Misconfigured WinRM can permit unauthorized remote management and control of OT devices.
OT Usage: Typically, remote management in OT is conducted through dedicated, secure channels.
Server Message Block (SMB) Protocol
Attack Vector: SMB vulnerabilities (e.g., EternalBlue) can be exploited to execute remote code, steal data, or propagate malware, especially when using outdated versions like SMB v1 and v2.
OT Usage: File sharing in OT is uncommon and typically conducted through more secure, controlled methods.
Windows Update Service
Attack Vector: This service looks for updates and installs them automatically. The implementation of automatic updates may result in the introduction of untested changes, which could potentially disrupt OT operations.
OT Usage: It is common practice to manage updates manually in order to guarantee compatibility and stability in OT environments.
SNMP (Simple Network Management Protocol)
Attack Vector: SNMP is employed for the administration and observation of network-connected devices. It can be used to gather detailed information about network devices, which can be exploited to launch targeted attacks.
OT Usage: Network management in OT is typically conducted through specialized, secure systems.
Telnet
Attack Vector: Telnet provides access to virtual terminals of remote systems on local area networks or the Internet. It transmits data in plain text, making it vulnerable to interception and exploitation.
OT Usage: Secure alternatives like SSH should be preferred for remote connections in OT.
It is strongly recommended that the services described above be disabled in an OT context whenever possible. If this is not a viable option, a risk assessment and suitable mitigation measures must be defined.
Mitigation Strategies
To mitigate the risks associated with Windows devices in OT networks, we recommend the following strategies:
Addressing these countermeasures can significantly improve the security posture of OT environments and protect critical infrastructure from potential cyber threats. The unique needs of OT networks require a tailored approach to managing Windows devices to ensure that industrial processes remain secure and uninterrupted.