Vulnerability for Your OT Security….
In CVE-2024-37998, NIST has identified a vulnerability in SICAM SCADA systems that could potentially allow an unauthorized individual to gain administrator rights on the OT systems. The criticality of this vulnerability has been classified as “critical”, due to the possibility of a remote attack, among other things. The corresponding security advisory was published on the Siemens website the day before, outlining the necessary measures to restore OT security. This issue has also been covered by a prominent German news portal.
It is not uncommon for vulnerabilities in OT components to go unnoticed by high-traffic, widely-read IT news portals. The fact that this report has made it may be due to the high criticality and prevalence of the affected OT systems. It is also reasonable to assume that, in the context of the NIS2 Implementation Act, the importance of OT systems for the national economy is being recognized more strongly. This would be a positive development. After all, critical systems are at great risk, are increasingly under attack, and need to be better protected .
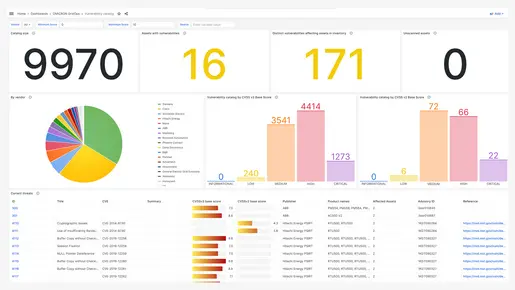
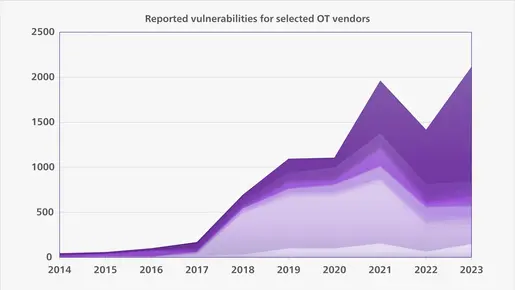
It is certainly NOT due to the limited number of OT vulnerabilities. Our OT vulnerability management system, which includes StationGuard and GridOps, has approximately 10 000 vulnerability reports on currently 25 manufacturers of OT systems.
…. and Countermeasures with
OT Intrusion Detection Systems
Vulnerability advisories from manufacturers also contain the necessary countermeasures to eliminate the risk, including software updates. It is imperative that these recommendations be followed without delay.
To do this, it is necessary to be aware of this vulnerability (1). Then you need to know which software version is being used on your OT systems (2). And then you also need to install the firmware update (3).
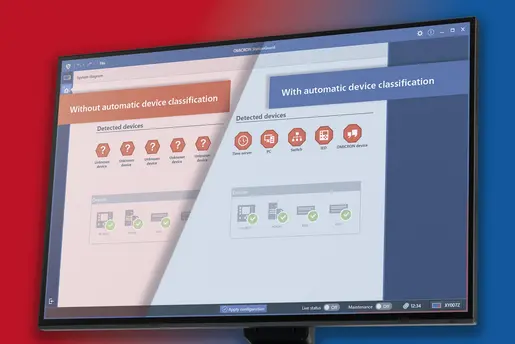
While (1) and (2) can be automated using suitable OT tools, patch management (3) presents a particularly challenging aspect of real OT operations.
The patching of OT systems is typically associated with a short-term (if all goes well) or sometimes extended (if not) loss of availability of the affected components. This necessitates long-term planning, as the component remains vulnerable until this occurs. Consequently, alternative measures are essential to mitigate the risk in the interim.
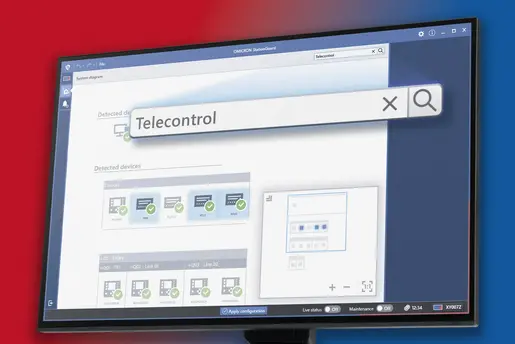
OT intrusion detection systems (IDS) help here. These systems are designed to continuously monitor the network traffic of substations, power plants, and control centers, identifying irregularities and potential threats. Specialized OT IDS eliminate the need for lengthy training periods, enabling rapid detection of anomalies as soon as they are activated.
The German government has also recognized the significance of IDS and has made it a mandatory requirement in §31 of the German NIS2 Implementation Act. The EU Commission's NIS2 Implementing Regulation (draft) also outlines the necessity for regular evaluation of data from security tools such as IDS.