Evolution of the
OT Vulnerability Landscape
The operational technology (OT) landscape has evolved dramatically in recent years. Historically, OT systems—encompassing industrial control systems (ICS), SCADA, and distributed control systems (DCS)—were secured by physical separation, or "air gaps," from IT networks. These systems prioritized reliability and physical security over network defenses and operated in isolated, specialized environments with minimal need for updates or connectivity.
Today, increasing demands for efficiency, remote monitoring, and IT-OT integration have reshaped this landscape. Modern OT systems are now deeply interconnected with corporate IT networks, enabling centralized management and data sharing but also broadening the attack surface. This convergence introduces vulnerabilities once confined to IT systems into the OT environment.
The complexity and connectivity of OT systems expose them to diverse cyber threats, including ransomware and advanced nation-state attacks. Compounding this risk is the reliance on legacy hardware and software in critical sectors like energy and manufacturing. These legacy systems lack built-in cybersecurity measures and often cannot be updated without disrupting operations, making patching a significant challenge.
OT vulnerabilities differ markedly from IT vulnerabilities, often stemming from insecure-by-design protocols and devices. These weaknesses can compromise physical processes, leading to safety risks, operational disruptions, and potentially catastrophic damage to critical infrastructure.
Key Findings of the OT Vulnerability Report
Building the OT Vulnerability Database
Through daily collection and analysis of OT-related vulnerabilities, we have established an extensive OT Vulnerability Database encompassing thousands of advisories and ten-thousands of vulnerabilities from all relevant vendors. This comprehensive dataset enables us to uncover critical trends and track the evolving threat landscape from 2009 to 2024, offering valuable insights into the vulnerabilities affecting OT environments.
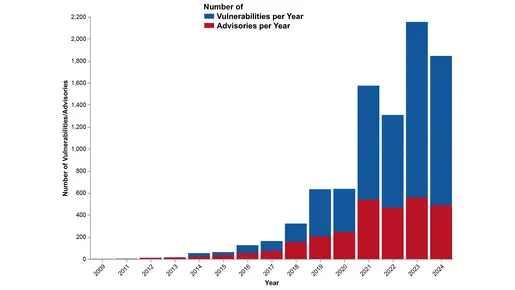
Vulnerability Growth
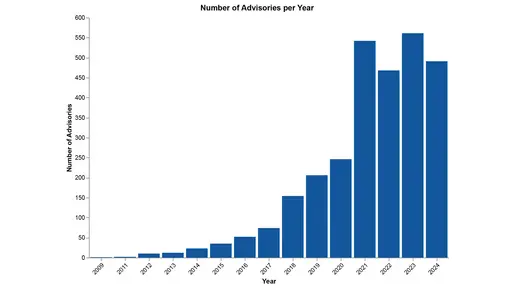
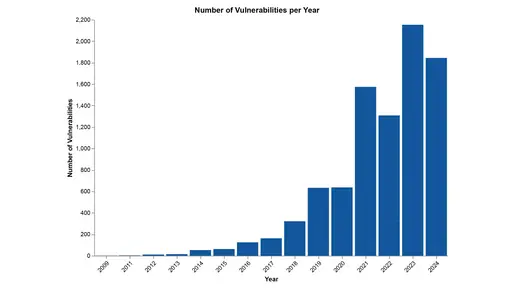
A year-by-year analysis of published security advisories and vulnerabilities reveals a consistent upward trend across all vendors. From 2009 to 2024, the number of advisories steadily increased, with a significant surge observed post-2017. This growth underscores the growing importance of addressing security issues in OT systems as their interconnectivity increases.
The most dramatic increases occurred in 2021 and 2022, when advisories nearly doubled compared to previous years. Two primary drivers contributed to this spike:
Vulnerability by Type
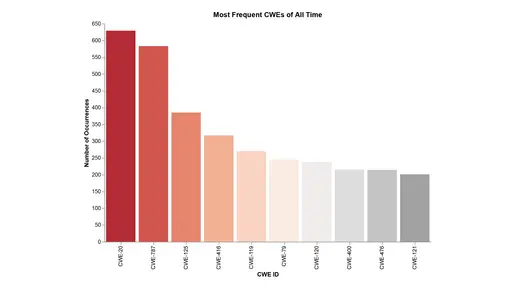
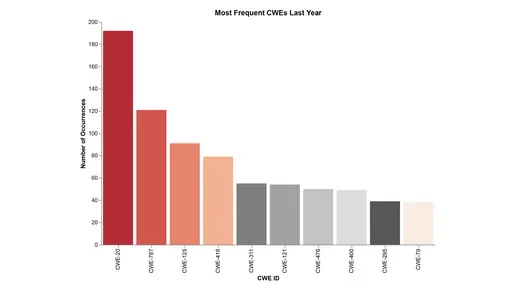
Security advisories aim to equip developers with the information necessary to identify and resolve issues while withholding critical details that could aid attackers in exploiting vulnerabilities. A key resource in understanding these weaknesses is the Common Weakness Enumeration (CWE), which categorizes vulnerabilities and helps map the attack surface.
Our analysis highlights two prevalent weaknesses that have remained significant over time:
Addressing Development Gaps
The root cause of these vulnerabilities often lies in insufficient attention to security during the development process. Practices such as proper input validation, rigorous data sanitization, and enforcing memory limits can help mitigate these issues. Integrating secure programming principles into product development is essential for reducing vulnerabilities.
Relevance to Broader Threat Landscapes
A comparison between these weaknesses and the OWASP Top 10 security risks highlights their continued relevance:
– CWE-20 aligns with OWASP risks like Injection (A03) and Insecure Deserialization, where improper input handling can lead to significant security breaches.
– CWE-787 correlates with issues such as Security Misconfiguration (A05) and other memory-related exploits, highlighting the importance of addressing these weaknesses across IT and OT systems.
These overlaps emphasize that vulnerabilities in OT environments are not isolated but rather part of a broader cybersecurity challenge that requires coordinated attention and secure development practices.
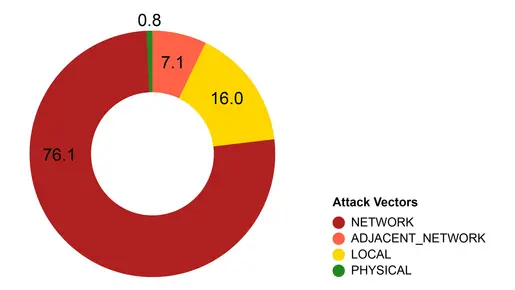
Predominant Attack Vectors
Our analysis reveals that network-based vulnerabilities account for over 75% of attack vectors in OT environments. These vulnerabilities allow attackers to exploit systems remotely, needing only network or internet access. This underscores the prominence of remote exploitation as the principal threat vector for OT systems. In contrast, vulnerabilities requiring physical access are minimal (<1%), reflecting how IT/OT integration and the reliance on network-connected devices have increased exposure to network-based attacks.
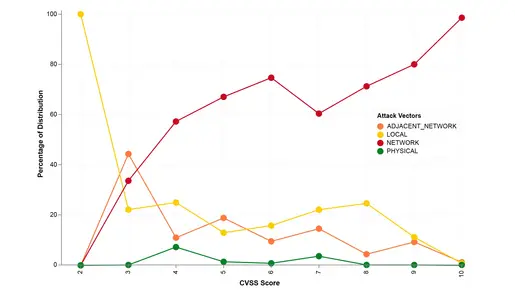
The severity of vulnerabilities, measured using CVSS scores, is closely linked to the associated attack vector. Network-based vulnerabilities typically have higher CVSS scores due to their widespread exploitability and significant impact potential. These vulnerabilities can bypass traditional perimeter defenses, posing a critical threat to OT systems that depend on continuous operation. Our data reveals that nearly all CVEs with a CVSS score of 10 are network-exploitable. Fittingly, only a small fraction of network-based vulnerabilities have low CVSS scores, showing the heightened risk they represent.
Quality of Security Advisories
The usability and effectiveness of security advisories vary significantly among vendors, complicating vulnerability management. While some vendors adhere to the Common Security Advisory Framework (CSAF) standard, others provide inconsistent formats or incomplete information, forcing substantial manual intervention. This disparity increases the complexity of aligning advisories with specific devices.
Two critical factors affect advisory quality:
1. Adherence to standards like CSAF ensures advisories are structured, machine-readable, and interoperable, reducing manual workload.
2. Accurate product and version identification enables quick matching of advisories to devices in an organization’s inventory, streamlining remediation efforts.
To bridge these gaps, we made significant efforts to improve advisory quality. This included:
– Adapting 10% of advisories to meet CSAF standards.
– Manually creating 22% of advisories, where vendors provided no machine-readable files.
These actions demonstrate the pressing need for industry-wide standardization in security advisories. Standardization not only reduces the burden on security teams but also improves the efficiency and effectiveness of vulnerability management.
For detailed guidance on using security advisories effectively, visit our resource: Advisories and How to Use Them.
Trends in the OT Vulnerability Landscape
The data reveals a steady increase in security advisories and vulnerabilities, particularly over the past decade. This rise reflects heightened security awareness, the influence of global events, and the discovery of critical flaws that prompt industry-wide attention. Additionally, the growing IT/OT integration has introduced new attack surfaces, accelerating the identification of vulnerabilities.
A concerning trend is the persistence of well-documented weaknesses in many products. Despite the availability of advanced solutions, these vulnerabilities remain widespread, indicating that they are actively exploited and will likely persist as threats.
Encouragingly, the adoption of the CSAF standard for writing and publishing security advisories has grown. This trend facilitates more efficient identification and management of vulnerabilities, streamlining processes for organizations and enhancing security outcomes.
Recommendations for
Mitigating OT Vulnerabilities
To address the evolving vulnerability landscape, organizations should consider the following steps to strengthen their defenses:
Given the challenging nature of implementing these recommendations, we advise prioritizing the following areas at the outset:
Comprehensive Asset Inventory
An accurate asset inventory is indispensable for effective vulnerability management. This database should include unique identifiers, manufacturers, models, firmware versions, IP/MAC addresses, and physical locations of each device. In particular, the product model and version should be written in the same format as described in the security advisory. This makes the matching process much easier and saves a significant amount of time.
Proper Collection of Vulnerabilities
To manage vulnerabilities effectively:
Vulnerability Management Tools
Vulnerability management tools are essential for automating and optimizing vulnerability workflows. Key benefits include:
Learnings from the
OT Vulnerability Report 2024
The fast-changing OT threat landscape calls for a proactive, structured, and collaborative approach to vulnerability management. As vulnerabilities grow in number and complexity, so do the risks to critical infrastructure. Advanced solutions like StationGuard GridOps empower organizations to manage vulnerabilities effectively by combining automation, accuracy, and actionable insights.
This report emphasizes the importance of unified efforts—across industries, teams, and systems—to secure OT environments. Only by prioritizing risk mitigation strategies and fostering collaboration, organizations can protect the essential systems that power modern society.
Information about
OMICRON's OT Security
OMICRON: Ensuring Data Accuracy with Innovative Processes
To verify their correctness of vulnerabilities and security advisories, we validate the CSAF files and PDFs provided by vendors, ensuring that corrupt or incomplete files are properly adjusted:
OMICRON: Ensuring Comprehensive OT Security with StationGuard GridOps
StationGuard GridOps, OMICRON’s specialized vulnerability management tool, is designed to meet the unique challenges of OT environments. It integrates directly with vendor and third-party advisory repositories, automating the collection and categorization of vulnerabilities. GridOps offers customizable dashboards that present real-time insights into vulnerability trends, remediation progress, and compliance with standards like the CSAF.
By leveraging GridOps, organizations can minimize the operational burden associated with vulnerability management. The tool ensures that critical vulnerabilities are identified and addressed promptly, enabling security teams to focus on maintaining the resilience and safety of their OT environments.
Important Terms
Read up on the most relevant terms in OT security:
Security Advisory
A security advisory is an official notification issued by a vendor, cybersecurity organization, or government agency that provides details about a specific security issue. It typically includes information about the vulnerability, the impact it could have, and recommendations for mitigating or resolving the issue. Security advisories are designed to alert users to potential threats and offer guidance on protecting their systems.
Vulnerability
A vulnerability refers to a flaw or weakness in a system, application, or network that can be exploited by an attacker to gain unauthorized access or cause damage. Vulnerabilities can exist in software, hardware, or even in operational processes, and they are often the subject of security advisories. Identifying and addressing vulnerabilities is a key part of cybersecurity, especially in OT environments where the impact can be critical.
OWASP
The OWASP Top 10 serves as a widely recognized standard for identifying and prioritizing critical web application security risks. This offers developers a roadmap for understanding and addressing the most pressing vulnerabilities. By aligning mitigation efforts with the OWASP Top 10, organizations can proactively reduce their exposure to these common and severe threats.
Common Vulnerabilities and Exposures (CVE)
CVE is a standardized identifier for vulnerabilities. Managed by the MITRE Corporation, a CVE number is assigned to each publicly known cybersecurity vulnerability. This number allows security professionals to communicate about specific vulnerabilities quickly and accurately across different tools, databases, and discussions. CVEs are used to track and address vulnerabilities consistently and are widely recognized across the industry.
Common Weakness Enumeration (CWE)
CWE is a list of common software and hardware weaknesses that can lead to vulnerabilities. While CVE identifies specific vulnerabilities, CWE categorizes the underlying issues that can lead to these vulnerabilities. For example, a buffer overflow vulnerability (CVE) might be categorized under the CWE for improper input validation. Understanding CWEs helps in identifying and mitigating the root causes of vulnerabilities.
CVSS Score (Common Vulnerability Scoring System)
CVSS is a standardized scoring system used to assess the severity of security vulnerabilities. The CVSS score ranges from 0 to 10, with higher scores indicating more severe vulnerabilities. The score is based on several factors, including how easy it is to exploit the vulnerability, the impact of exploitation, and the complexity of the attack. CVSS scores are used to prioritize vulnerability management efforts, helping organizations focus on the most critical issues first.