Is Your Critical Infrastructure
Network Less Secure
than Your Wi-Fi?
On your home Wi-Fi, only devices that provide the correct password can communicate with the other devices on your private network. With a good passphrase, brute-force access can make it difficult for an unauthorized person to gain access. Similar security measures would be expected in critical infrastructure networks such as power substations, and gas and water pumping stations. However, to date, probably 99% of these networks would allow you to simply plug your laptop into one of the Ethernet switches and send commands to the critical control devices on the local network. These systems are completely dependent on the physical security of the building around them. If you look at the substations in your neighborhood, you will notice that many of them have simple doors and sometimes no fence or camera.
An adversary could gain direct access to critical local plant control by plugging into one of these switches and planting malware on the devices to execute a (time-)coordinated attack. Substation networks are typically connected to larger networks that link control centers, power plants, and substations. By plugging into a network switch at a remote substation, an adversary could use this as an attack vector to the control center.
Many OT security policies and regulations require the implementation of Network Access Control (NAC) measures on the Ethernet network switches in critical automation networks. We have heard several times that auditors checking compliance with local laws for the EU NIS Directive (version 1.0) require the use of 802.1X NAC on these critical automation networks.
While 802.1X may provide effective security in business networks, its applicability in OT networks may be limited.
How Does Network Access Control (NAC) Work?
There are numerous ways to implement Network Access Control (NAC). NAC methods typically involve verifying the identity of the user or device and then allowing or denying network access based on that information. However, all of these methods can be circumvented or bypassed. Before we demonstrate how this could be done with 802.1X, let's first cover some fundamental concepts.
In the case of corporate IT, there are several options available with regard to NAC. It can be implemented at the switch level, where the switch port is either activated or deactivated, or moved into different VLANs (guest VLANs), based on the authentication result. Alternatively, NAC can be implemented at higher network levels, for example by restricting access to IP addresses from the DHCP server, or by setting different firewall rules for each client.
A key functionality of numerous NAC systems in corporate IT environments is the ability to monitor client behavior. In the event of an unexpected change in the way a VoIP phone operates, for instance, the NAC can swiftly move the device into a quarantined VLAN.
In substation OT networks, for example, the options for NAC technologies are limited because DHCP is typically not used, and there is no possibility of installing any software on the automation devices. Consequently, NAC must be implemented at the Ethernet switches.
The Limitations of MAC-Based Access Control in OT Networks
One common method of implementing NAC in OT networks is by utilizing the MAC address of the device in question. The switch maintains a list of authorized MAC addresses and will only permit access if the device's MAC address is recognized as a known device. One advantage of this method is that it is relatively straightforward to implement. One disadvantage of this approach is that maintaining the list of MAC addresses is a time-consuming process. It is not sufficient to add only the devices in the automation network; all engineering laptops and spare devices for replacement must also be included.
It is crucial to maintain a comprehensive list of authorized devices, as on-duty engineers must be able to replace malfunctioning devices at any time, including weekends or night shifts. Technicians should not be required to enter the MAC addresses of replacement devices into all Ethernet switches. The most significant drawback of MAC-based access control is that it can be circumvented with relative ease through the manipulation of an approved device's MAC address. It is relatively simple to perform MAC spoofing.
Some network card drivers allow users to change their MAC address directly in the Windows network settings. When two devices in the network have the same MAC address, communication issues may arise because the switch is unable to determine which switch port the packets should be forwarded to. In some cases, the original device may become unable to receive packets, which could potentially lead to a denial-of-service situation in an automation network.
It is therefore important to activate the Port Security setting on the switch as a countermeasure. This feature prevents a second device on a different port from using the same MAC address. Consequently, the attacker must unplug the original device, copy its MAC address, and then plug in their impostor device for MAC spoofing to be effective. While the attacker can still gain access to the network, the unplugging of an automation device is typically detected and flagged by the local RTU and SCADA system.
This begs the question of whether it is worth the effort to maintain MAC address lists for MAC-based access control when you can simply enable port security on the switches.
Can 802.1X Stop MAC Spoofing in OT Networks?
IEEE 802.1X enhances security by requiring devices to authenticate themselves to an authentication server before the switch port is opened. This authentication is typically used in conjunction with device certificates but can also be implemented using usernames and passwords. This is an effective defense against the MAC spoofing attacks described earlier. The disadvantage is that an authentication server, such as RADIUS (Remote Authentication Dial-In User Service), must be introduced into the automation network. In the case of certificate-based authentication, it is necessary to ensure that all devices have the correct certificates deployed and the ability to manage certificates in the future. In addition, not all automation devices support IEEE 802.1X, which limits its activation to select ports on your switch.
The main problem is that 802.1X can also be easily bypassed by using Ethernet injection with MAC spoofing.
How Does Ethernet Injection with MAC Spoofing Work?
An attacker can use several methods to gain access to a network, such as password phishing on Wi-Fi networks, device injection, or physical access via an Ethernet cable. In all of these methods, the attacker is identifiable on the network by his MAC address and IP address. A network intrusion detection system will detect the new MAC address and trigger an alert for the new device added to the network. To avoid being seen on the network, attackers can use MAC spoofing. The same technique can be used to bypass 802.1X.
Ethernet Injection with MAC Spoofing is a method of silently connecting an attacker's device to the network and sending messages using the MAC address and physical Ethernet connection of a legitimate device on the network. This is accomplished by disguising packets from the attacker's device and merging them with those from the legitimate device over a single shared physical Ethernet connection. From the perspective of the switch and the network, there is only one device with a single physical cable transmitting packets using the legitimate MAC address.
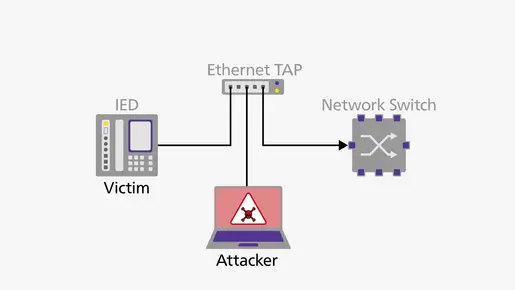
To circumvent 802.1X, the attacker physically positions themselves between the legitimate device and the switch, effectively acting as a conduit for all packets between the two. This can be achieved through the use of an Ethernet TAP (Test Access Port) with traffic injection functionality. Alternatively, an Ethernet hub can be employed for 100 Mbit connections, which remain widely utilized in OT networks.
Once the link has been re-established, the legitimate device will re-authenticate using 802.1X, after which the switch will open the port. At this point, the attacker can inject packets by spoofing the MAC address of the legitimate device. However, if the attacker makes a mistake and sends packets without the spoofed MAC address, the switch will drop the packets and may raise an alert.
How Can Attackers Apply Ethernet Injection with MAC Spoofing in OT Networks?
To bypass 802.1X, an Ethernet TAP with a traffic injection function is used. The workflow would look as follows:
How to Identify MAC spoofing attacks in Your OT System?
If the attacker has physical access to the network, MAC spoofing represents a highly effective attack strategy. It is therefore necessary to implement additional detection tools to recognize this attack. One highly effective tool for detecting such attacks is a network-based IDS, ideally with an allow list (whitelist) approach. An IDS with deep-packet inspection and an allow list approach allows network administrators to specify which messages from each device are permitted, restricting the protocols and services that can be used. If the attacker's actions differ from those of the spoofed device, this will trigger an IDS alert, seriously limiting the potential options for the attacker.
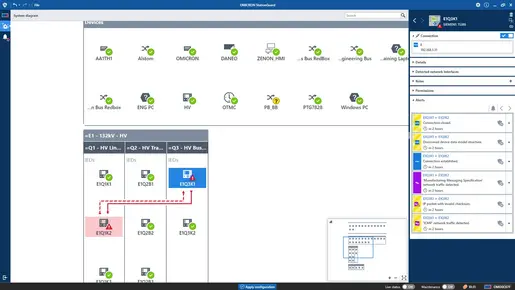
StationGuard is an OT Intrusion Detection System, specifically designed for use in OT Networks in power plants, substations, and control centers. In addition to detecting threats via an allow list approach and analyzing communication in depth, StationGuard has configurable roles for most power grid automation device types, allowing users to precisely define the allow list for each device. This allows network administrators to set up the allow list with minimal effort while maximizing the ability to detect Ethernet injection and spoofing attacks in power grid networks. Furthermore, StationGuard is capable of identifying modified packets that violate the operating configuration. This is especially beneficial in OT networks, where packets are frequently sent unencrypted and in plain text within the network.
How Physical Security and Network IDS Can Counter MAC Spoofing Risks?
Ethernet injection with MAC spoofing attacks represent an effective method for conducting undercover communication within a network. In particular, in the context of power grid OT networks, where the majority of communication is not authenticated, this attack represents a significant risk.
As illustrated by the examples, these attacks can be executed with minimal effort and are highly effective. However, they require physical access to network equipment or devices. This highlights the necessity of robust physical perimeter security for electrical power substations. It is also crucial to restrict physical access to LAN cables and patch panels within substation relay houses to deter potential attacks. Ethernet injection with MAC spoofing can often evade ordinary detection systems or firewalls. Allow list-based network IDS, such as StationGuard, are vital tools for detecting such attacks.